IoT Series (I): Are People Ready to go?
In recent years, advances in the area of the Internet of Things (IoT) have evolved at an extremely high rate, and it is becoming increasingly difficult not to be surrounded by an IoT device, including in our own homes.
As we know, novelties are increasingly attractive in today’s world, and technology already occupies a large percentage of the lives of almost every citizen of the world.
However, are people prepared for such a rapid evolution? Are people sufficiently educated about the technological risks?
This first article intends to raise awareness to the common user, while the next articles in the series, go deep into the technology and therefore more suited to IT and cybersecurity professionals.
What is the Internet of Things?
When we think about what the devices belonging to the IoT niche really are, we become aware of how many of these types of devices there are around us.
The Internet of Things refers to devices that are in our daily lives that interact with the Internet, and possibly with each other.
Connected cars, home security systems, smart sensors, smart refrigerators, smart bicycles, voice-controlled speakers, and so on.
Connected to the Internet? Probably someone is trying to mess with it.
Today, there are a staggering amount of devices connected to the Internet. But is this a problem? It could be. These days it is easy for anyone to plug in a device in their own home or for simple entertainment and have the same device connected remotely via the Internet, but this leads down another path, if it is Internet-faced, it is publicly available – to everyone.
Although the type of situation described above is increasingly easy, there is still a lack of security posture on the part of users, and this can jeopardize aspects of their own lives, including exposure, data theft, or control by malicious people.
One of the biggest demonstrations of the lack of cybersecurity posture are cameras connected to the Internet.
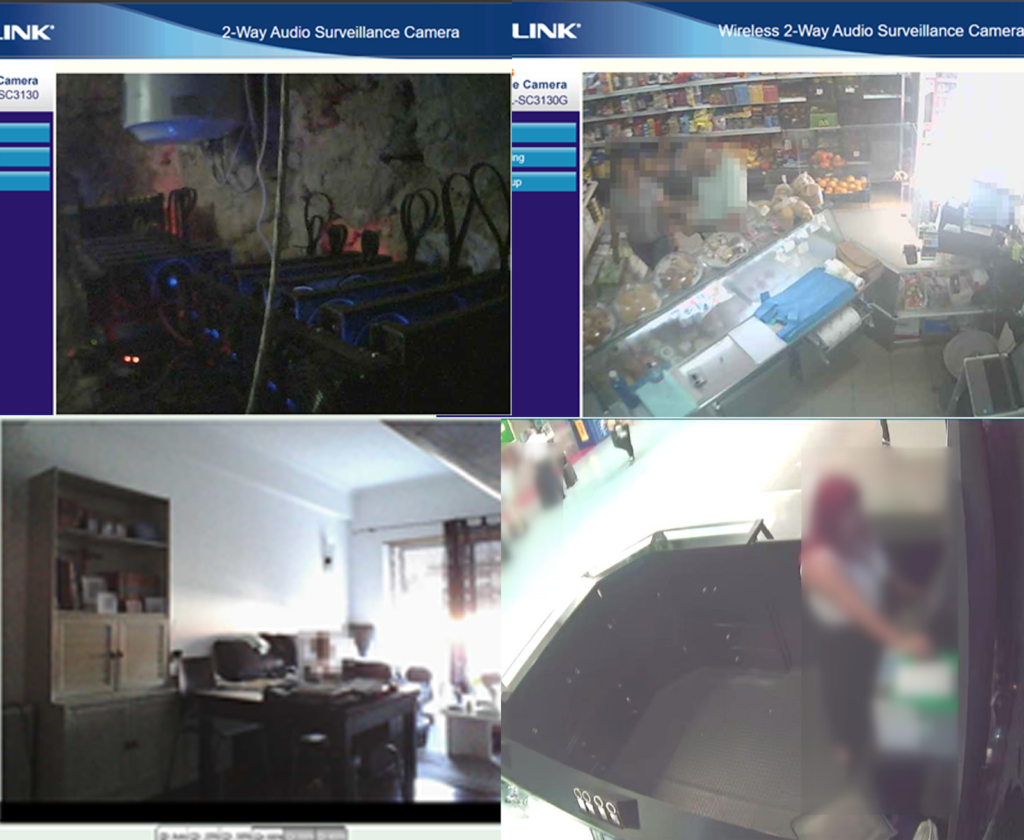
With extremely fast searches and without highly elaborate methods, it is possible to find a huge variety of online cams accessible to anyone through their login interface. Adding this to another extremely common mistake: not changing the default passwords on these devices or using passwords that are extremely easy to guess, is a recipe for disaster.
By performing one of these searches, it is possible to find all kinds of cameras as presented below.
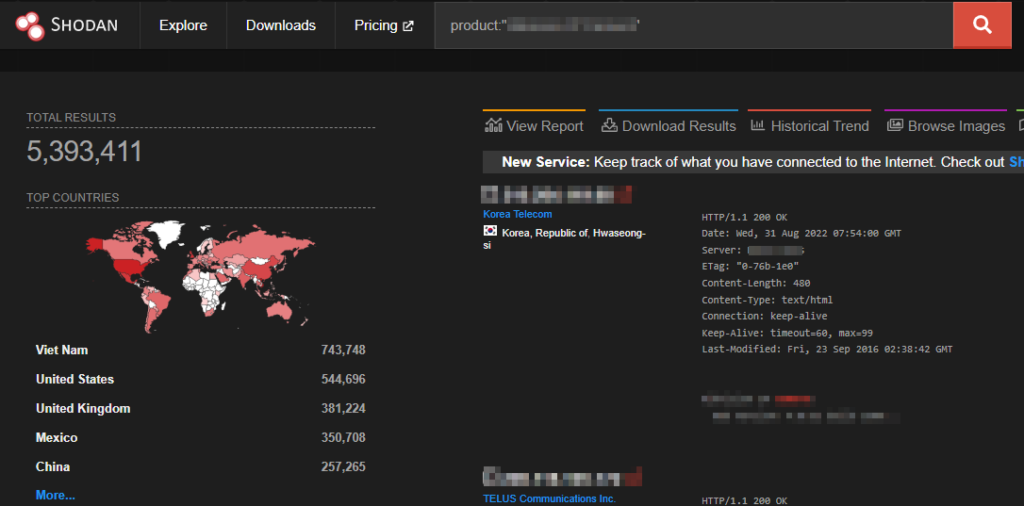
Performing a simple search – on one of the most well-known internet scanning databases (Shodan) – by one of the top surveillance cameras manufacturers yields a large number of results. These represent, in fact, cameras, or control systems, exposed directly to the internet.
Smart Homes: Evolution or insecurity?
Both. As we have talked about earlier in this article, both aspects are very present in IoT systems. On one hand, the extraordinary evolution of being able to perform one-click actions away from home, on the other hand, there is (still) a lack of end users basic security when it comes to their devices.
The ease of insertion and deployment of IoT devices by a normal user means that situations like the following exist more and more:
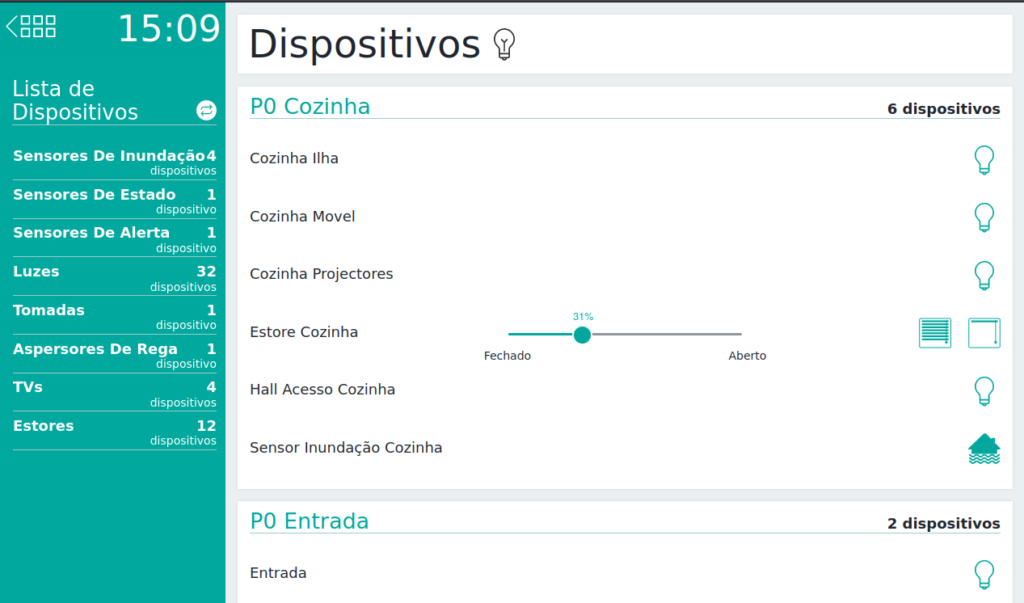
As seen, a fully automated home system (lights, blinds, security systems, irrigation system, televisions, sensors) with the default password in use and available to the entire Internet as observed.
Like this situation, there are many others. For example, exposed sensors:
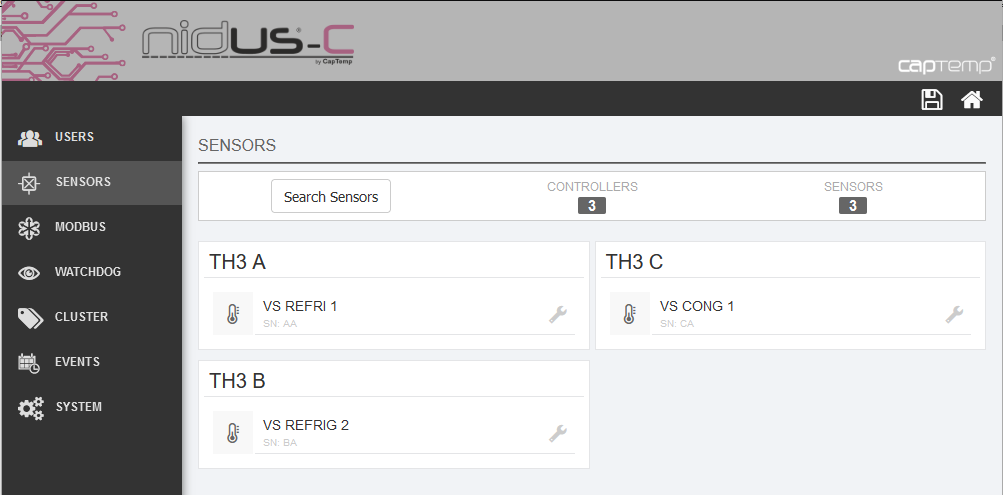
The most common mistake is the failure to change the password that comes by default. By searching the web, we can find thousands of connected devices related to smart homes with this problem.
The Goldmine: Routers

For everything to work intelligently in our home, there is one thing that is almost indispensable: a router.
The Internet router in our home connects us to the web and allows us to contact devices no matter how far away we are. If these devices are available with a public address, we can already imagine what happens.
Routers can be a gold mine for a malicious actor. Dozens of options are available to tinker with the device and network, and by allowing access to the router, a malicious actor is practically “inside our house.”
These devices are probably the most easily found online around the world and again with the same problem as other IoT devices, the default passwords.
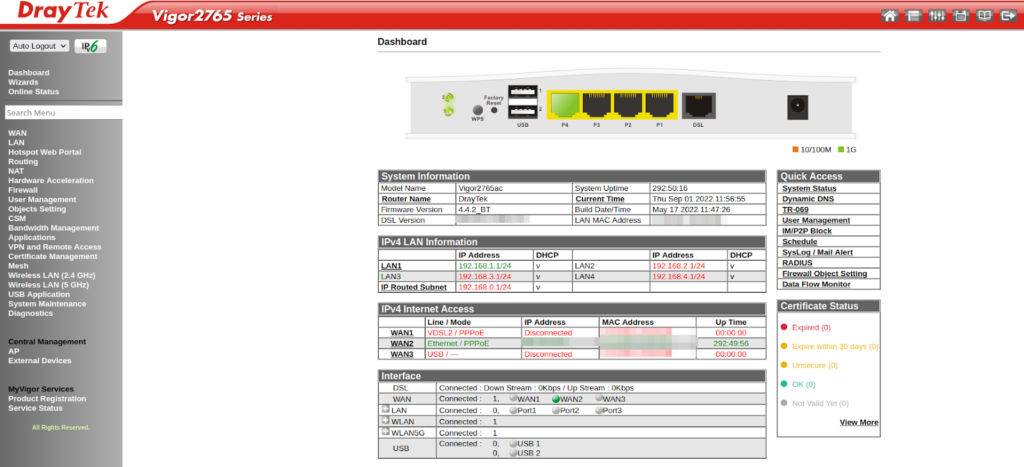
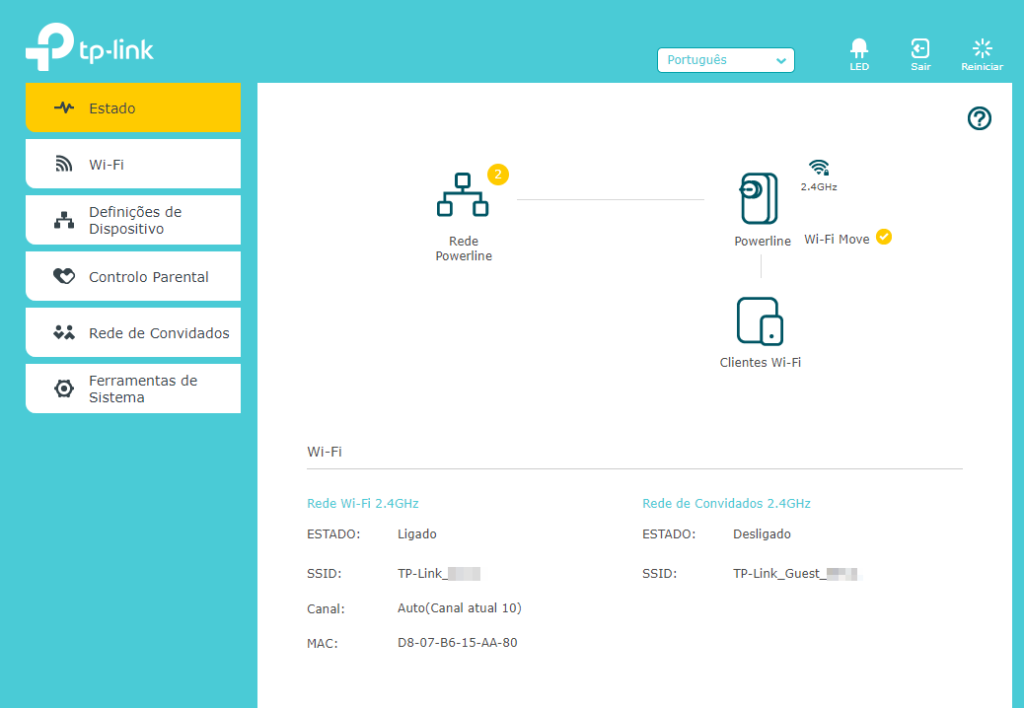
Default passwords: only problem?
Although default passwords are probably the most common security flaw, there is one thing we must not forget: vulnerabilities in the software of the devices.
During the last few years, a huge number of flaws have been found in various devices, and we can see a sample of this using for example disclosed vulnerabilities that contain the “router” word:
https://cve.mitre.org/cgi-bin/cvekey.cgi?keyword=router+
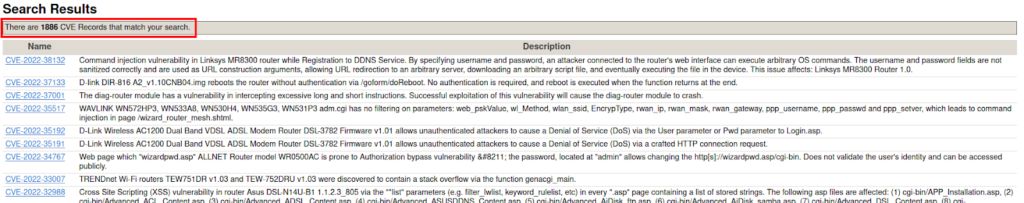
Therefore, one more point to teach the average user will be the need to allow these devices to stay up to date by performing the appropriate updates if possible.
Regulations and Guidelines
Recently there have been proposals for regulations for digital elements, including by the European Commission.
Regulations
EU Cyber Resilience Act is a proposal for legislation governing cybersecurity standards for products containing digital elements, covering both hardware and software.
A very comprehensive article on how this act will influence the IoT world can be found at the following link:
EU announces first ever move to legislate cybersecurity for IoT
The Cyber Resilience Act can be downloaded from the following page:
Cyber Resilience Act | Shaping Europe’s digital future
Guidelines
The GSMA provides a guideline file with about 85 recommendations for secure design, development, and deployment in IoT systems:
GSMA | IoT Security Guidelines Overview Document | Internet of Things
ENISA has also shared a very complete file with several recommendations for IoT security:
ENISA Report – Guidelines for Securing the Internet of Things.pdf
Conclusions
As we have seen, despite all the evolution that we are observing daily in technology, an extremely important aspect that is not yet implemented in our society is the need to understand and use cybersecurity measures.
The mindset insertion of two basic aspects of cybersecurity – default password changes and the use of complex passwords, as well as system security patching – are small tasks that greatly promote cybersecurity in IoT devices.
This will also make sense on the part of device owners and developers. One measure already visible in some situations is the need to create a new password when the system is accessed for the first time.
On the other hand, the usage of cheap and low-tech components can introduce or open the door to new flaws. For instance, the simple usage of cryptography on devices with low processing power can have a serious impact on the performance of the device, but at the same time, it poses a serious risk to its safety.
Are you ready for the next IoT series article?
IoT Series (II): How to build kernel image from scratch
IoT Series (III): Firmware testing in QEMU
IoT Series (IV): Debugging with GDB & GHIDRA
Author
Bernardo Rodrigues